Highlights
- Security graphs enable fast multi-hop traversals to trace indirect access from users through groups and roles to sensitive resources, spotting over-permissions and cleaning up IAM sprawl with tools like FalkorDB's OpenCypher queries.
- FalkorDB's sparse-matrix engine delivers p99 latency 496x faster than alternatives, supporting in-memory analytics for entitlement audits and lateral movement simulation across millions of nodes without performance hits.
- Build schemas capturing entities like users, policies, and events, then run queries to visualize exposure paths, IP-based access patterns, and toxic privilege combos, streamlining CSPM and threat detection workflows.
Why Security Needs Graph Thinking
If you’re working in IT or security today, you already know the landscape is anything but simple. Every user is tied to roles, which link to groups, which inherit permissions across resources that may be scattered across multiple clouds. Additionally, the number of users, cloud resources, permissions, and policies seems to grow every week, and everything is connected in ways that are hard to keep track of. In most cases, this is managed using multiple cloud IAM dashboards. However, even though IAM dashboards can show direct permissions, they rarely expose the indirect chains of access that attackers look for. This makes cloud security fairly challenging to manage, especially as the number of users grows.
That’s where security graphs come in. Instead of trying to force all those relationships into rows and columns, a security graph lets you map users, resources, roles, and policies as nodes, and shows how they’re all connected. Suddenly, the big questions get a lot easier to answer, like:
- Who can (even indirectly) get into a sensitive resource?
- Which outside systems does this service depend on?
- Are there users with more access than they should really have?
To make this work in practice, you need a database that can handle complex, fast-changing relationships without slowing you down. That’s where FalkorDB comes in. It’s designed for speed, scale, and ease of use, so you can analyze your security environment in real time, no matter how large or complicated things get.
What you’ll get from this article:
- What a security graph actually is (with examples)
- Why graphs are better than old-school databases for this kind of work
- How you can set up a security graph yourself (using FalkorDB)
- How we chose what to model and why
- Real-world use cases, and where to go from here
By the end, you’ll know what security graphs can do for you, and have a clear starting point for building one that works for your own environment.
Inside a Security Graph: Nodes, Edges, and Metadata
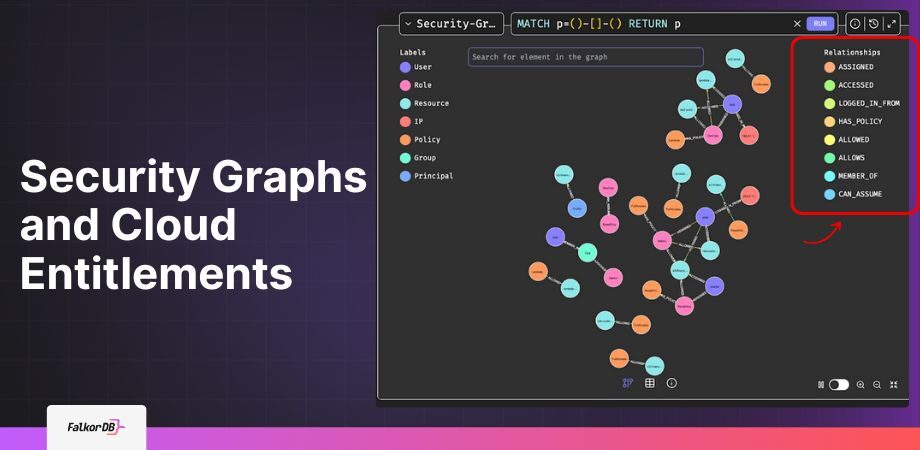
A security graph is a data model built to capture the tangled, real-world relationships between users, roles, permissions, policies, resources, and activities, all as a connected network of nodes and edges.
Here’s how it works:
- Nodes stand for security-relevant entities like users, roles, policies, resources, or permissions.
- Edges (relationships) show how these entities are linked; for example: who grants what, who belongs to which group, which policy applies, or what activity was logged.
- Properties can be added to nodes and edges to capture extra details, such as timestamps, severity, or permission levels.
A simple example:
- Node: User: Alice
- Node: Resource: Database1
- Edge: (Alice) —[HAS_ACCESS {method: “IAM”}]→ (Database1)
With a structure like this, you can answer tough questions in milliseconds, such as:
- Does Alice have direct or indirect (transitive) access to Database1?
- Which high-risk policies are active on production systems?
Security graphs make it possible to see and query these relationships instantly, even as your environment grows and changes.
“Graphs can turn your tangled security data into a living, interactive map, making it possible to spot risks and answer tough questions in real time.” Roi Lipman, CTO, FalkorDB
Why Use a Graph for Your Organization's Security?
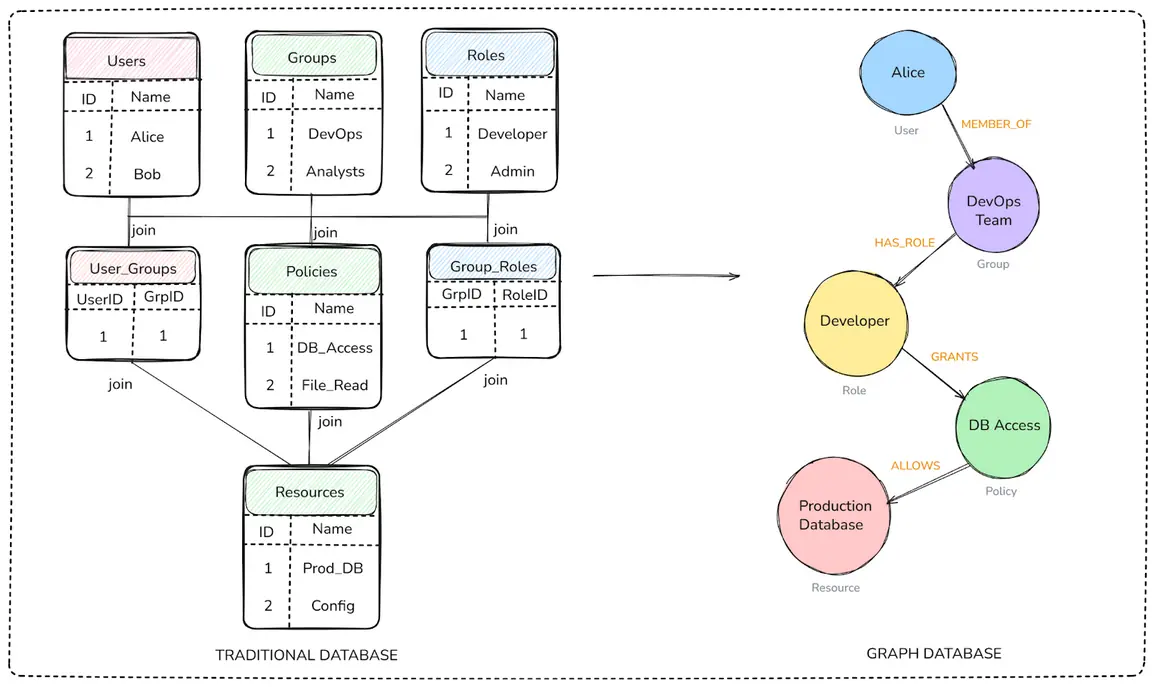
Traditional databases, whether SQL or NoSQL, organize information into rows, columns, or key-value pairs. That works fine for simple, flat, or strictly hierarchical data. But security data rarely fits into neat boxes. In real-world environments, you’re dealing with:
- Many-to-many relationships (like users with multiple roles, or roles that grant multiple permissions)
- Deep, indirect connections (such as user → group → role → policy → resource)
- Constant change (users join, roles shift, resources and permissions are added or removed)
Graph databases are built for this kind of complexity.
- Relationships are first-class citizens; they don’t need workarounds like JOIN tables.
- Multi-hop traversals (across even the most nested or indirect links) are fast and efficient.
- Security teams can finally see the big picture, mapping how users, policies, and resources are actually connected.
Put simply, graphs can turn your tangled security data into a living, interactive map, making it possible to spot risks and answer tough questions in real time.
Why Graph Databases Power Security Systems
When you’re building or querying a security graph, you’re dealing with entities and relationships — how users map to roles, policies connect to resources, and how access flows across complex paths. A graph database like FalkorDB is built for exactly this kind of data.
What Sets FalkorDB Apart
- Sparse Matrix + Linear Algebra Engine
FalkorDB represents the graph internally as sparse matrices and uses linear algebra operations for querying. This architecture enables ultra-fast, scalable traversals across millions of nodes and edges with minimal memory overhead – ideal for identifying indirect access paths or privilege escalation scenarios. - OpenCypher Support with Optimizations
FalkorDB implements the standard OpenCypher query language (plus a few proprietary extensions), making it intuitive for security teams familiar with graph queries. It includes commands like GRAPH.PROFILE and GRAPH.EXPLAIN to debug query plans and optimize performance in real-world environments. - In-Memory Performance with Persistence
FalkorDB runs in memory but persists data to disk, giving you real-time query performance without sacrificing durability. This combination is essential for scenarios like entitlement analysis or lateral-movement detection, where every millisecond counts. - Multi‑Tenancy at Enterprise Scale
FalkorDB supports co-located multiple graphs (tenants) within a single instance. Each environment remains fully isolated for security and governance, while sharing the same infrastructure for efficiency. - Rich Graph Analytics & Built‑In Algorithms
Beyond simple queries, FalkorDB offers graph algorithms like label propagation (CDLP), betweenness centrality, weakly connected components (WCC), and shortest path analysis — enabling threat and lateral-movement detection directly in-database.
Why Relational or NoSQL Databases Fall Short
- Schema rigidity and JOIN Pain
SQL/NoSQL databases handle relationships via join tables or embedded documents — a cumbersome and often inefficient approach when dealing with access graphs that change rapidly or require multiple hops to trace. - Complexity Escalates Quickly
Building systems to answer questions like “Which users could indirectly access this resource?” requires multi-level joins and deep subqueries, often leading to poor performance, convoluted queries, and missed insight. - Limited Graph Reasoning Capabilities
Even if relational systems support some graph-like querying, they lack native support for graph analytics (like shortest-path or centrality) — making them challenging to build algorithms where graph reasoning is required.
What This Means for Security Use Cases
- Access Path Analysis
Security teams can rapidly determine whether a user has direct or indirect access to a resource, even across deep chains (e.g., User → Group → Role → Policy → Resource). - Least Privilege Auditing
You can quickly flag over-permissioned identities or unused roles and simplify entitlement reviews through graph traversals. - Threat Detection & Lateral Movement
Built-in path and community algorithms help model attacker movement potential, detect suspicious privilege escalation paths, and visualize risk relationships.
Security Graph Use Cases
Security graphs deliver real results across a range of modern security challenges. With a graph database like FalkorDB, organizations can move from static reports and scattered spreadsheets to living, queryable maps of their security landscape. Here’s how security teams are using security graphs in practice:
Cloud Infrastructure Entitlement Management (CIEM)
Cloud environments grow fast and change constantly. It’s easy to lose track of which users, roles, and services have access to what. Identity sprawl, excessive permissions, and inherited access can put your entire organization at risk.
A security graph makes cloud entitlements fully visible by mapping relationships between cloud users, groups, roles, and resources in real time. With a system built using graph databases, you can:
- Find users with excessive or outdated permissions
- Pinpoint unused roles and clean up over-provisioning
- Enforce least privilege policies with simple, expressive graph queries
Result: Audits are easier, compliance gets smoother, and risk drops dramatically.
Cloud Security Posture Management (CSPM)
CSPM is all about continuous oversight of your cloud environment to spot security gaps, misconfigurations, and policy violations before attackers do.
Security graphs let you visualize the entire infrastructure, including cloud assets, configurations, dependencies, and even risky changes, as a connected, always-up-to-date map. Using FalkorDB:
- See how resources are interconnected (and where single points of failure may lurk)
- Surface misconfigurations or assets missing critical controls
- Automate compliance checks and policy enforcement as your environment evolves
This bird’s-eye view makes it easier to predict, prioritize, and address risks across your cloud footprint.
Identity and Access Management (IAM)
IAM is about understanding the web of relationships between users, groups, roles, and the resources they touch. These relationships are inherently a graph problem.
With a security graph, you can:
- Map every user, group, and role, and see their access paths
- Detect risky privilege combinations or role overlaps (“toxic combinations”)
- Trace and review who can access sensitive resources, directly or indirectly
You can use FalkorDB to build a security graph of your system, that helps security teams review access, catch anomalies, and keep permissions lean and well-audited.
Threat Detection and Lateral Movement Analysis
Attackers rarely go straight for the prize: they move laterally, exploiting weak links and privilege escalation opportunities. Traditional tools struggle to map these potential attack paths in a changing, interconnected environment.
Modeling your infrastructure as a graph makes it possible to:
- Identify all possible paths an attacker could take from initial access to sensitive systems
- Simulate breach scenarios and visualize privilege escalation risks
- Spot and remediate the weakest links before they’re exploited
FalkorDB’s high-speed graph traversal and analytics help you build security systems that can allow for proactive defense, helping you outthink attackers, not just react to them.
Benefits of FalkorDB for Security Graphs
Unmatched Real-Time Performance
FalkorDB is a graph database where the graph architecture is designed as a sparse-matrix with linear-algebra engine, delivering ultra-fast responses, even under large-scale production workloads. Benchmark tests show p99 latency up to 496× faster than Neo4j, making FalkorDB ideal for security operations that demand split-second access reviews, entitlement checks, and lateral movement tracing.
Memory-Efficient and Transparent
Features like string interning help deduplicate repeated metadata, keeping memory use lean in graphs with millions of users, roles, and resources. The GRAPH.MEMORY USAGE command provides a detailed breakdown of memory consumption by nodes, edges, and indices, supporting fine-grained performance tuning and easy capacity planning.
True Multi-Tenancy by Design
FalkorDB supports multiple fully isolated graphs (“tenants”) within a single instance, enabling organizations or SaaS platforms to separate environments or keep customer datasets isolated, which is essential for MSSPs, regulated industries, and complex enterprise orgs.
Scales with Your Data
Whether your environment is doubling every quarter or changing minute-by-minute, FalkorDB is designed for high-velocity, ever-evolving security data. Features like robust array indexing, configurable query memory limits, and rapid ingestion allow it to handle permission and resource churn without missing a beat.
Advanced Graph Algorithms
FalkorDB includes production-ready algorithms for label propagation (CDLP), weakly connected components (WCC), and betweenness centrality, letting security teams:
- Detect user/resource communities
- Find potential attack pivots or privilege escalation points
- Simulate breaches and automate exposure scoring—all without exporting data
FAQ
What are security graphs in cloud environments?
Security graphs model entities as nodes (users, roles, resources) and relationships as edges (assignments, policies), allowing queries to reveal direct and transitive access paths for entitlements management in AWS or GCP setups.
How do security graphs improve threat detection?
They map lateral movement risks via shortest-path algorithms and community detection, simulating attacker pivots from initial breaches to critical assets, with FalkorDB enabling real-time analysis of privilege escalation chains.
Why choose FalkorDB for building security graphs?
FalkorDB offers linear-algebra optimizations for scalable traversals, multi-tenancy for isolated graphs, and built-in algorithms like betweenness centrality, making it ideal for high-velocity security data in enterprise IAM.