6 Reasons you need a graph to store your security data
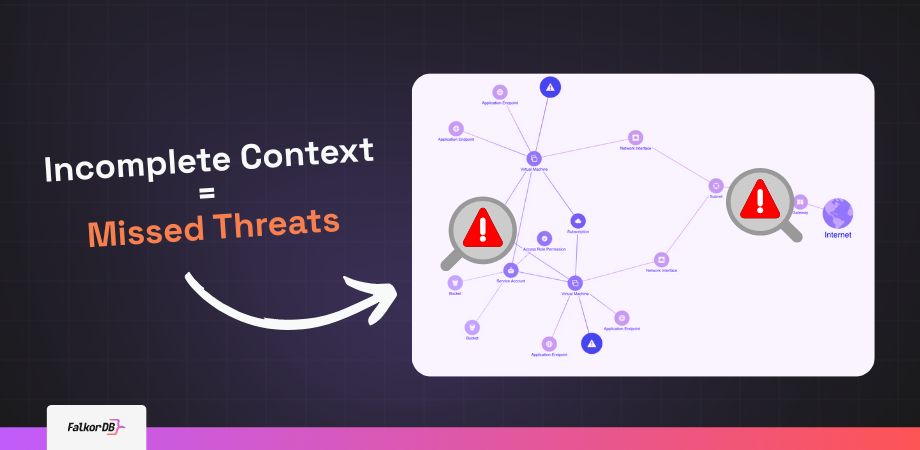
As a Cloud Security vendor, you’re building protection systems for environments that constantly change. Your customers deploy across containers, serverless, ephemeral compute, and IaC pipelines. You need to correlate misconfigurations, permissions, and runtime signals across identity, network, and workload layers, at scale, in real time, without losing performance or exceeding the scoped operational costs. That’s where graphs come in.


