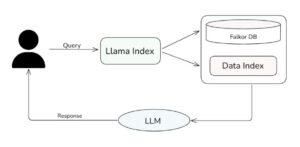
Extending FalkorDB with User-Defined Functions and FLEX
FalkorDB introduces user-defined functions (UDFs) written in JavaScript, allowing developers to extend graph database functionality with custom logic. FLEX library provides pre-built functions for text processing, similarity metrics, and date manipulation.